
My guess is that when a request is made without the SNI TLS extension, the Akamai edge environment reports a TLS error. Sadly, Akamai reports this TLS error using the TLS internal_error(80) fatal alert code instead of the more descriptive missing_extension(109). That's because missing_extension(109) wasn't defined until TLS 1.3 (which is much more expressive of the reason for failure).
On my side, I had half-enabled SNI, where it was used for the main protocol request and response, but wasn't being used for the requests sent to the underlying authorization protocol (OAuth 2.0). The reason that was missed was simply because it is a completely independent module.
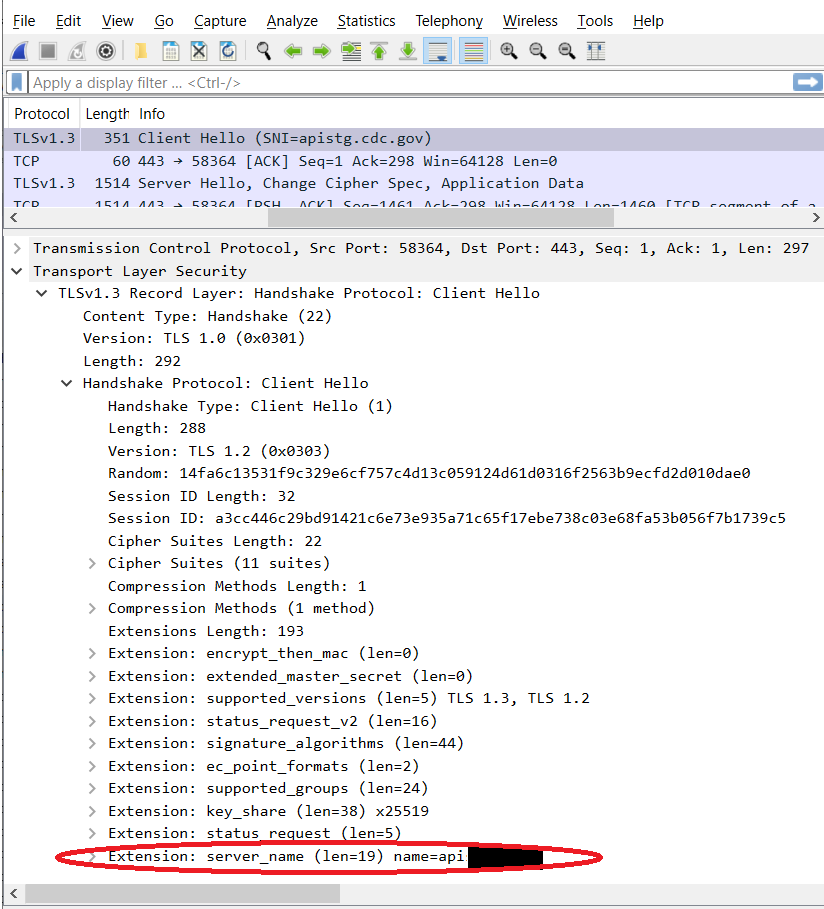
If you've got WireShark, and you see something like this in your capture, look at the list of extensions.
If server_name extension is missing, as in the above capture, you need to fix your code to use SNI. Once you've fixed it, it should look like this:
In any case, if you are using BC FIPS, and get an internal_error(80) while trying to connect to an Akamai Edge Server, and your TLS Client Hello doesn't contain the SNI Extension: Well, there's your problem.


0 comments:
Post a Comment